
In recent years, Cyber Risk has been undergoing continuous transformation in terms of regulations, technologies, and methodological approaches.
This transformation is often addressed by building increasingly structured and coherent models, reference frameworks, clearly defined policies, and procedures designed to cover every possible scenario. This has helped organizations bring structure to a complex domain—a necessary step that, in many cases, has proven effective.
Today, however, an important limitation is emerging in these models: they describe how risk should be managed under stable conditions, when the context is predictable and time is not a critical factor. In real operational environments, things rarely unfold this way. Alerts may arrive when services have already stopped working, the incident is already underway, and threats have already produced their impact.
In such moments, Cyber Risk Management becomes a sequence of decisions that must be made quickly, often with incomplete information and limited room for maneuver. What becomes essential is the organization’s ability to orient itself within a changing scenario, where priorities shift rapidly and someone must take responsibility for deciding first what to do and how to do it.
The five questions below fit into this perspective and provide a lens through which to observe risk as it takes shape in an organization’s daily activities, amid operational decisions and concrete responsibilities.
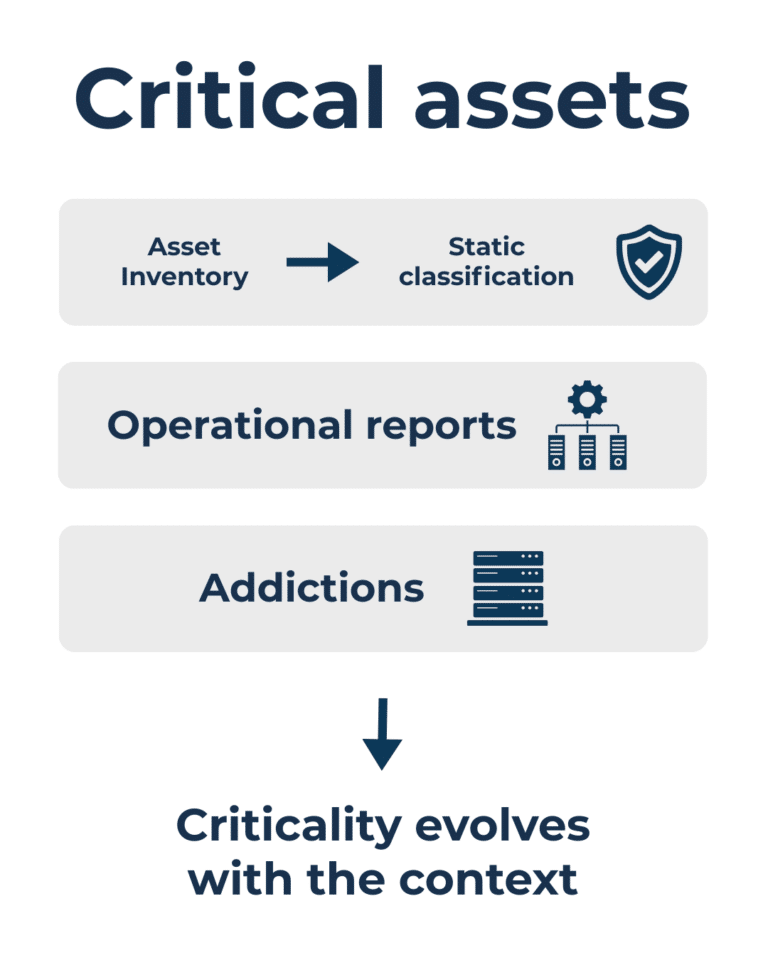
Almost all companies can list their assets. Many can also classify them by criticality. The problem arises when moving from theory to operations. An asset may be classified as critical because it was in the past, or because it is considered so “by definition,” yet it may have lost part of its real importance over time. Conversely, a marginal asset can become central due to how it is connected to other systems or processes.
The criticality of an asset often emerges gradually, following the evolution of the operational context. Systems originally designed as secondary can, over time, assume a central role, supporting functions that become essential—without this shift always being formally recognized.
Many incidents originate in areas considered secondary, where attention has gradually shifted elsewhere. In these contexts, risk tends to grow quietly, without immediate signals. Asset inventory remains an essential foundation, but real criticality emerges from how an asset is embedded in the operational context and from the relationships it develops, rather than from the label assigned during an initial assessment.
An asset becomes critical because of how it operates within the system, not because of how it is classified in a document.
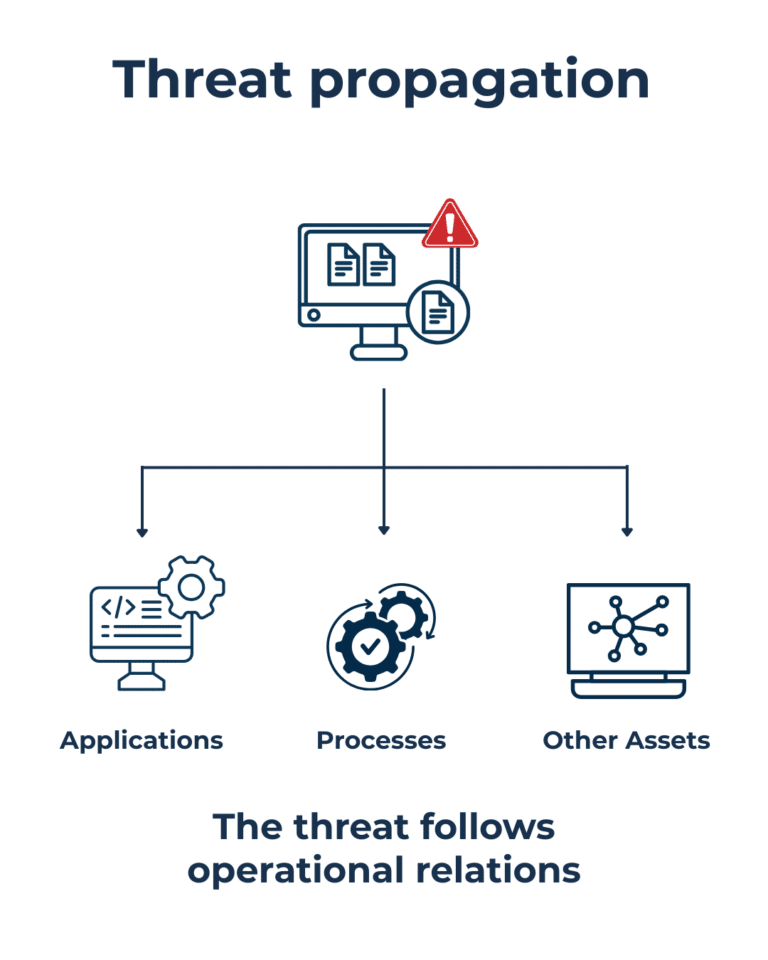
This is perhaps the most underestimated question in traditional Cyber Risk Management. For years, attention has focused primarily on entry points: where an attacker can gain access, which vulnerability can be exploited, which system is most exposed. All valid questions, but partial ones.
In today’s context, the real risk is not so much where a threat enters, but how far it can go. Modern infrastructures are built on relationships, network communications, application dependencies, and system integrations that, individually, function correctly. Risk moves and propagates along these relationships.
A siloed view struggles to capture this phenomenon. Analyzing one system at a time provides a sense of control that is often illusory. A threat rarely remains confined to the initial asset. It propagates by exploiting what the infrastructure allows it to do, not what is theoretically intended.
Understanding propagation means observing risk as a dynamic phenomenon that traverses the system along paths that are often undocumented. It means asking not only “what happens if this asset is compromised,” but “which other assets and processes are affected downstream.” In this sense, risk must be analyzed through the set of relationships that make it exploitable. This is where many organizations realize they do not truly understand how their assets interact with one another.
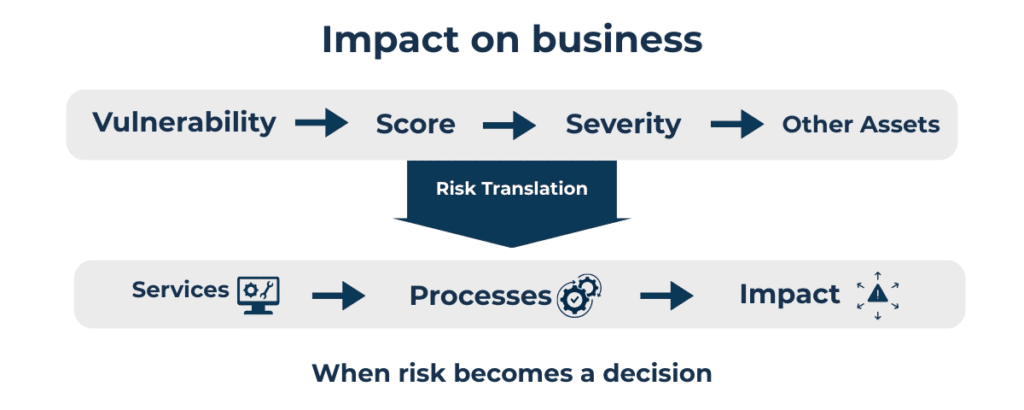
Another critical issue concerns how risk is communicated within the organization. Technical metrics are plentiful: vulnerabilities, scores, and severity levels are produced with great precision. What is more difficult is turning them into information that genuinely supports decision-making. Too often, they remain confined to specialist language—technically correct, but of limited use outside that domain.
Risk begins to matter when it is interpreted in terms of its impact on the organization’s day-to-day operations. When it affects services, processes, and responsibilities, it stops being a purely technical assessment and starts entering the discussions that drive decisions. When risk cannot be read in these terms, it struggles to become a topic of discussion at the executive level. It remains something to be monitored and controlled, but rarely something that shapes informed choices. The discussion stops short of decisions.
This type of understanding comes from a different approach, one focused on how risk evolves over time and the effects it may produce. Attention shifts toward reconstructing the context in which risk operates, its possible evolutions, and the ability to make consequences and choices visible.
A risk that does not lead to decisions remains a technical data point, even if it is accurate.
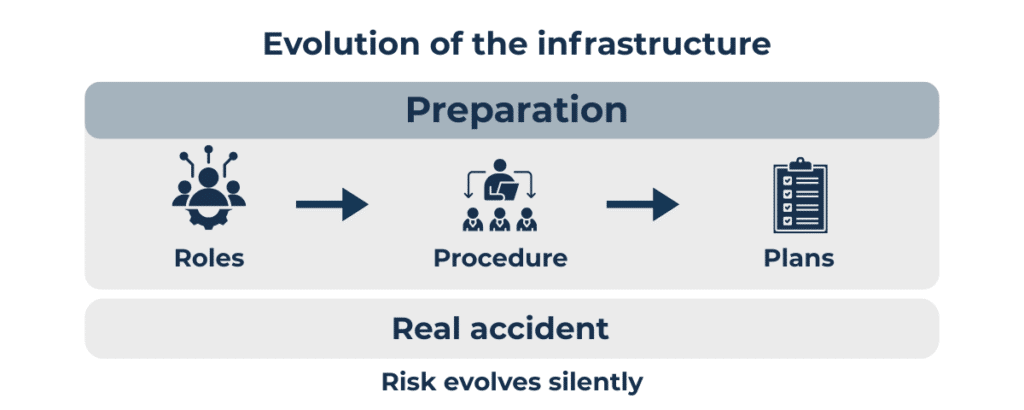
One of the most common misconceptions is thinking of risk as something that changes only in the presence of an attack. In reality, risk evolves every time the infrastructure evolves. Routine changes, progressive integrations, or new operational relationships can alter overall exposure without producing immediate signals.
Many risk models accurately describe the situation at the moment they are built, but struggle to remain aligned over time. As months pass and the infrastructure evolves, that representation gradually loses its connection to operational reality. The issue is not the quality of the assessment, but the continued trust placed in a picture that is no longer updated.
Governing Cyber Risk requires the ability to read infrastructure evolution and understand its impact on risk, even when change occurs silently.
A real incident is the moment when all organizational fragilities surface. Roles that are formally defined often overlap, responsibilities become unclear, and the time available to act shrinks dramatically. This is where Cyber Risk Management is tested in its most concrete form.
The NIS2 Directive makes this aspect even more explicit by introducing the role of the CSIRT Contact Point. Not merely as a point of contact, but as an operational hub in incident management—a figure who must coordinate, communicate, make decisions, or support them under high pressure.
The real value of the CSIRT Contact Point lies above all in the clarity of the role and in actual competencies. This role must clearly understand what decisions can be made autonomously, when escalation is required, which information must be collected, and how it should be communicated.
A cyber risk team’s true capability emerges when someone must decide quickly, with incomplete information, and assume real responsibility. If this moment is not governed, everything built beforehand loses much of its value.
The five questions presented here serve to measure an organization’s real maturity in terms of its ability and readiness to act. They reveal whether Cyber Risk Management is a living discipline, capable of adapting, or whether it has remained a formal exercise.
In 2026, Cyber Risk will increasingly move away from compliance and become a true operational test of organizational value. What will matter is not only what has been declared, but what an organization is able to respond to when the context truly demands it.
Because governing risk today primarily means being ready to make concrete, informed decisions.
Within this scenario, ESRA positions itself as an operational support for those responsible for Cyber Risk Management. ESRA enables the observation of risk within the real infrastructure context, following the evolution of assets, relationships, and dependencies that determine exposure.
Through continuous and contextual analysis, ESRA helps identify what is truly critical today, how a threat can propagate, and how technical changes modify the risk profile. It makes risk readable and governable within the real operational environment.
In a context where Cyber Risk is increasingly a matter of decisions and responsibility, ESRA supports those who must orient themselves, evaluate scenarios, and choose how to act.
ai.esra SpA – strada del Lionetto 6 Torino, Italy, 10146
Tel +39 011 234 4611
CAP. SOC. € 50.000,00 i.v. – REA TO1339590 CF e PI 13107650015
“This website is committed to ensuring digital accessibility in accordance with European regulations (EAA). To report accessibility issues, please write to: ai.esra@ai-esra.com”
ai.esra SpA – strada del Lionetto 6 Torino, Italy, 10146
Tel +39 011 234 4611
CAP. SOC. € 50.000,00 i.v. – REA TO1339590
CF e PI 13107650015
© 2024 Esra – All Rights Reserved